Single sign-on
Users can use SSO to log in to Mitzu. For that, Mitzu first needs to be configured with the company SSO. You can configure the following SSO providers:
- AWS Cognito
- Google SSO
- Any OIDC (OpenID Connect) compatible authentication backend like Okta, OneLogin
AWS Cognito
Create a new app client in AWS Cognito
- Log in to Mitzu and navigate the 'Account settings' page. Once SSO is enabled, you can configure the details of the integration:
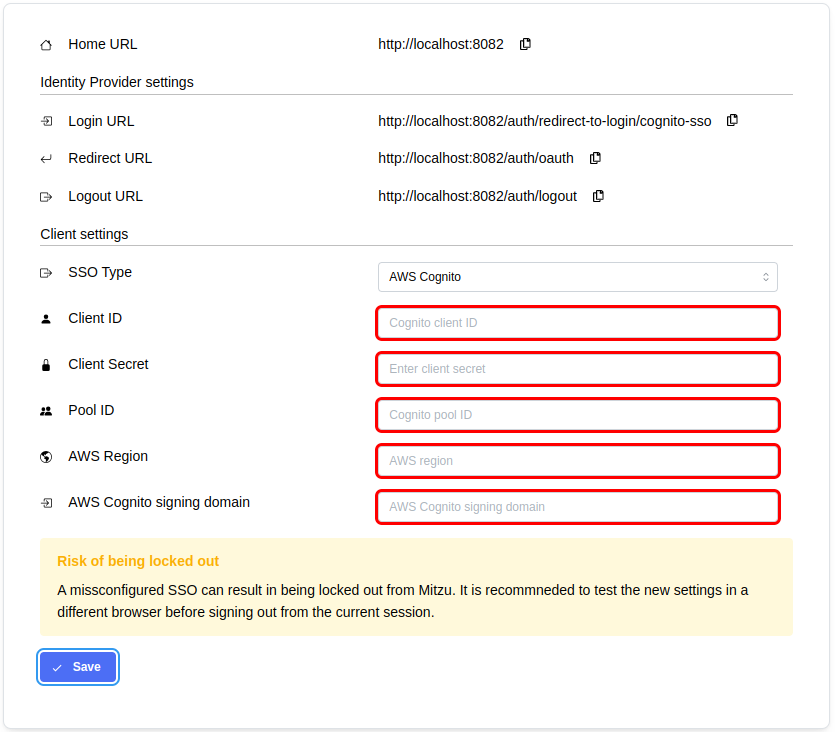
- Open the AWS Console and create a new app client to your AWS Cognito user pool with the following settings:
- Auth type: Confidential client
- Allowed callback URLs: copy the entire value of the Redirect URL input from the Mitzu SSO settings
- OAuth 2.0 grant types: Authorization code grant
- OpenID connect scopes: Email must be selected
Configure Mitzu with the Cognito app client
- Configure the client settings on the Mitzu SSO page
- Client ID and Client Secret values can be found on the app client settings page
- Pool ID, AWS Region, and AWS Cognito signing domain can be found on the user pool settings page
- Click save
Google SSO
Create a new app client in Google
-
Log in to Mitzu and navigate the 'Account settings' page. Once SSO is enabled, you can configure the details of the integration:
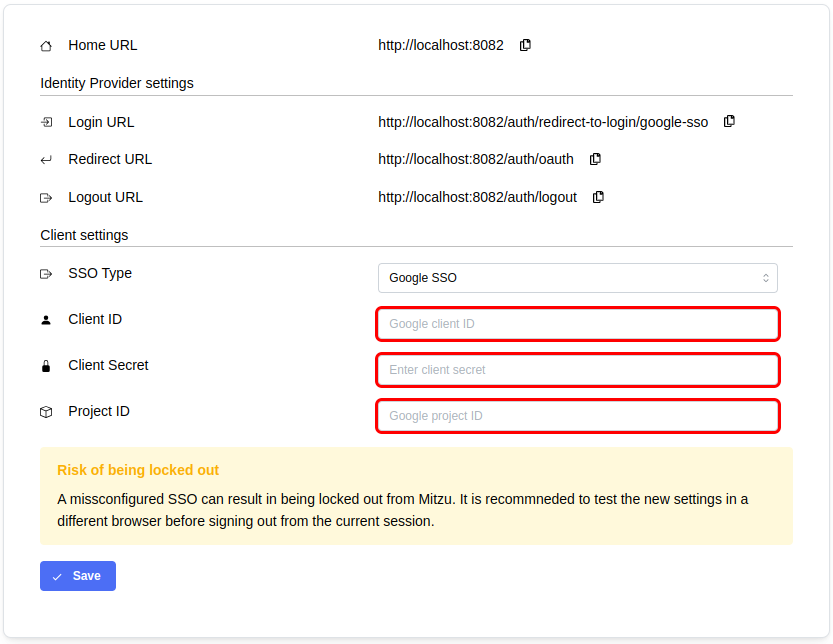
-
Open the Google Cloud Console and create a new OAuth 2.0 Client ID (on the APIs & Services -> Credentials page) with the following settings:
- Application type: Web application
- Authorized redirect URIs: copy the entire value of the Redirect URL input from the Mitzu SSO settings
Configure Mitzu with the Cognito app client
- Configure the client settings on the Mitzu SSO page
- Client ID and Client Secret values can be found on the app client settings page
- Project ID can be found on the Cloud Overview -> Dashboard page in the project info box
- Click save
OIDC
Create a new app client in your Identity Provider
- Log in to Mitzu and navigate the 'Account settings' page. Once SSO is enabled, you can configure the details of the integration:
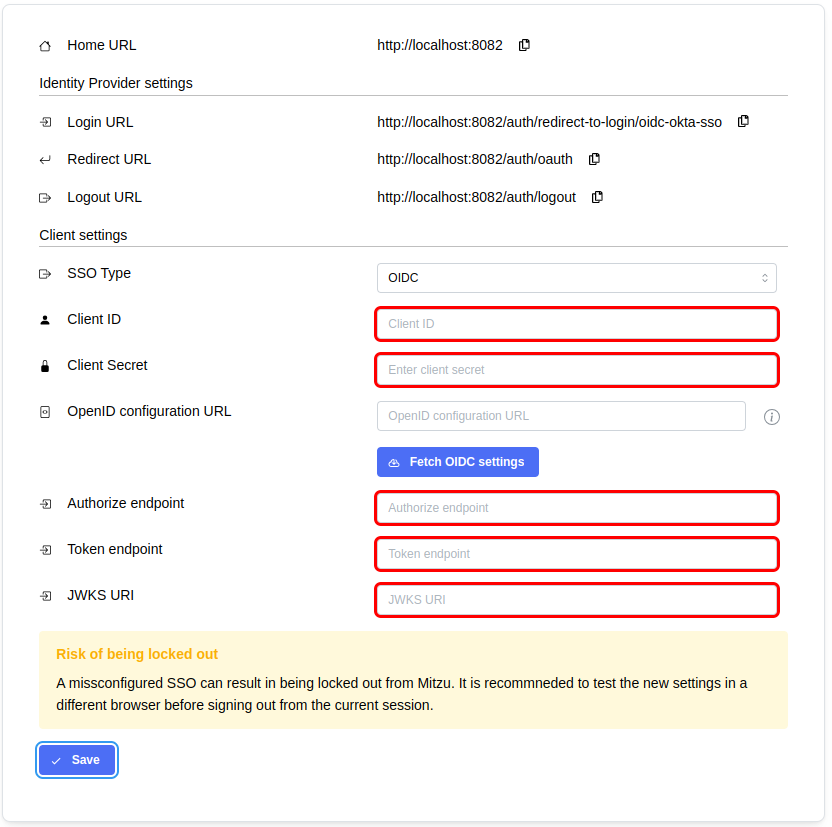
- Open the web console of your Identity Provider and create a new client application with the following settings:
- Application type: Web Application
- Grant type: Authorization Code
- Sign-in redirect URIs: copy the entire value of the Redirect URL input from the Mitzu SSO settings
- Sign-out redirect URIs: copy the entire value of the Home URL and append `/auth/unauthorized'
- to initiate the login from the Identity Provider side, redirect the users to the Home URL appended '/auth/redirect-to-login'
- Client authentication: client secret
Configure Mitzu with the OIDC app client
- Configure the client settings on the Mitzu SSO page
- Client ID and Client Secret values must be found on the selected OIDC app client's settings page
- Authorize endpoint, token endpoint, and JWKS URI can be configured manually or set the
<idp>/.well-known/openid-configurationURL and click on the Fetch OIDC Settings button. It will fetch the configuration and fill out these fields.
- Click save
Verify login flow
In a different browser (or in an incognito window) verify the login flow. If it is not working as expected then please supervise your settings or contact Mitzu Support.